Two weeks ago, Square launches its own bug bounty program that rewards external security researchers starting from $250, no maximum bounty reward is stated though.
I reported a couple of bugs but most of them were tagged as duplicated. As of the moment, I earned just $750.
Now, I’ll be sharing 2 XSS in Square’s appointments.
Square Appointments is a new online tool by Square to provide simple booking experience that lets businesses manage appointments, save time and avoid losing sales from customers.
The tool is actually announced publicly by Square, few days after it announced its bug bounty program. I accidentally stumbled upon an article of the news while searching about Square, in connection to mapping my program target – Square Inc.
Simple XSS in setting up business website:
In Square Appointments’ setting, public profile, you are asked to provide your business website.
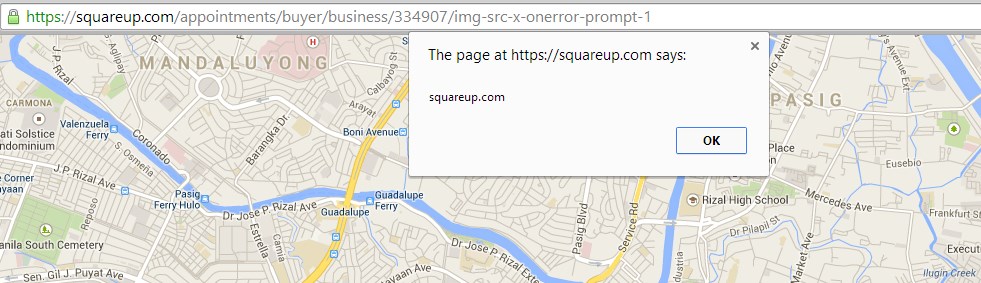
I input javascript:alert(document.cookie) in business website field and submit.
That escalated quickly! There is no error upon saving my business field set up as javascript:alert(1). The javascript vector executes upon clicking the business site link located at the bottom right side of my booking site.
Bypass the Client Side block for XSS execution!
Pretty easy right? I thought of testing the other input fields, the Facebook profile and the Twitter username.
Tested the same vector now, javascript:alert(document.cookie) but it ends up caught on client-side error – not Facebook and or Twitter URLs!
Did you notice it? I mentioned of client-side error, It could meant, the server was not doing the same way!
So, for the bypass and served as Proof of Concept ( POC ):
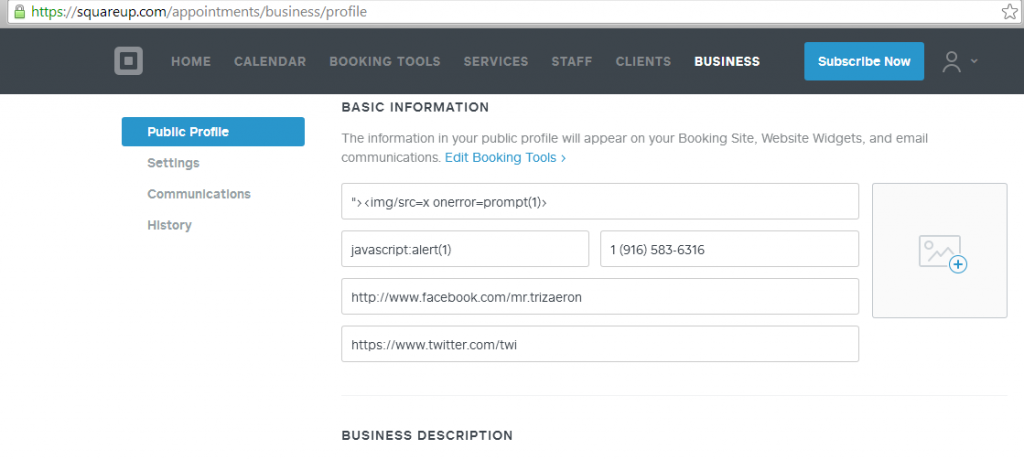
1. Go over to https://squareup.com/appointments/business/profile
2. Input https://www.facebook.com/sample in the Facebook Profile field and https://twitter.com/sample in the Twitter URL field.
3. Click on Save ( You must have intercepted the request, I use BURP )
4. Modify the URLs for Facebook and Twitter inputted on the fly, as for me I changed it to javascript:alert(/forFacebook/) and javascript:alert(/forTwitter/) respectively.
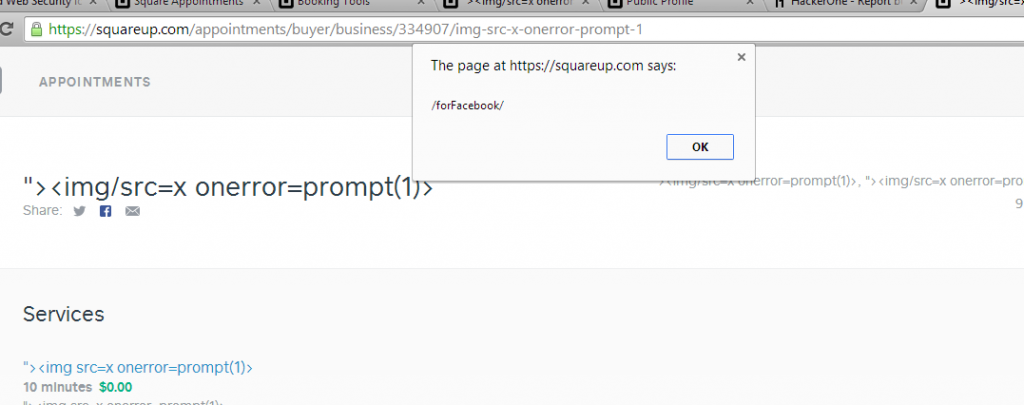 It executes upon clicking the social media icons in the “Share” menu.
It executes upon clicking the social media icons in the “Share” menu.
Saved! We bypassed it by modifying our request on the fly changing the social media URLs to our vector.
For information, the block is only in the client side and does not happen on the server side, it must be on both. Client side blockage can be trivially bypassed.
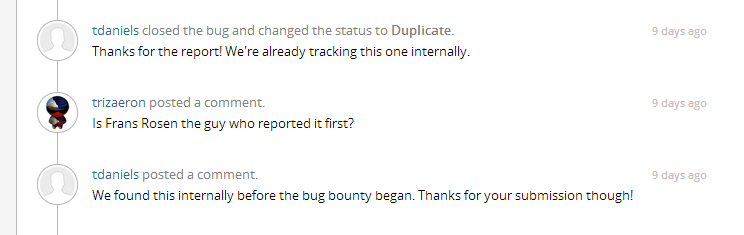
Unfortunately, even those bugs are both valid there was no reward issued since its tagged as duplicated. Here is what the Square security team stated.
Note: The XSSs are fixed now!
You may want to visit my Hackerone Profile, www.hackerone.com/trizaeron.